*************<NOTE: Please be aware that Windows 10 and 11 do not support Software Restriction Policies any more. If you have the Professional version or better for either operating system you can now use AppLocker. You can read how to set that up here... END NOTE>***************
Today I'm going to show you how to setup a Group Policy Object to prevent random software packages running under the users profile or other locations not authorised by you, the system administrator.
Why is this important? It's important because, with prevalence of ransomware and other invasive malware, Software Restriction Policies will help you prevent these type of things running on your network.
Please note, that this does not replace the need for good anti-virus software, properly configured network security, network firewall and users from being local admins of their PCs.
I highly recommend that no users are local admins for the very reason that this will bypass this policy and enable them to run software unencumbered.
Before you roll this across your network create a Test OU so you can just apply it to a select number of PCs to evaluate the functionality so that it is not too restrictive for your environment. This, effectively gives you time to iron out any bugs and whitelist applications that need special considerations.
Let's begin...
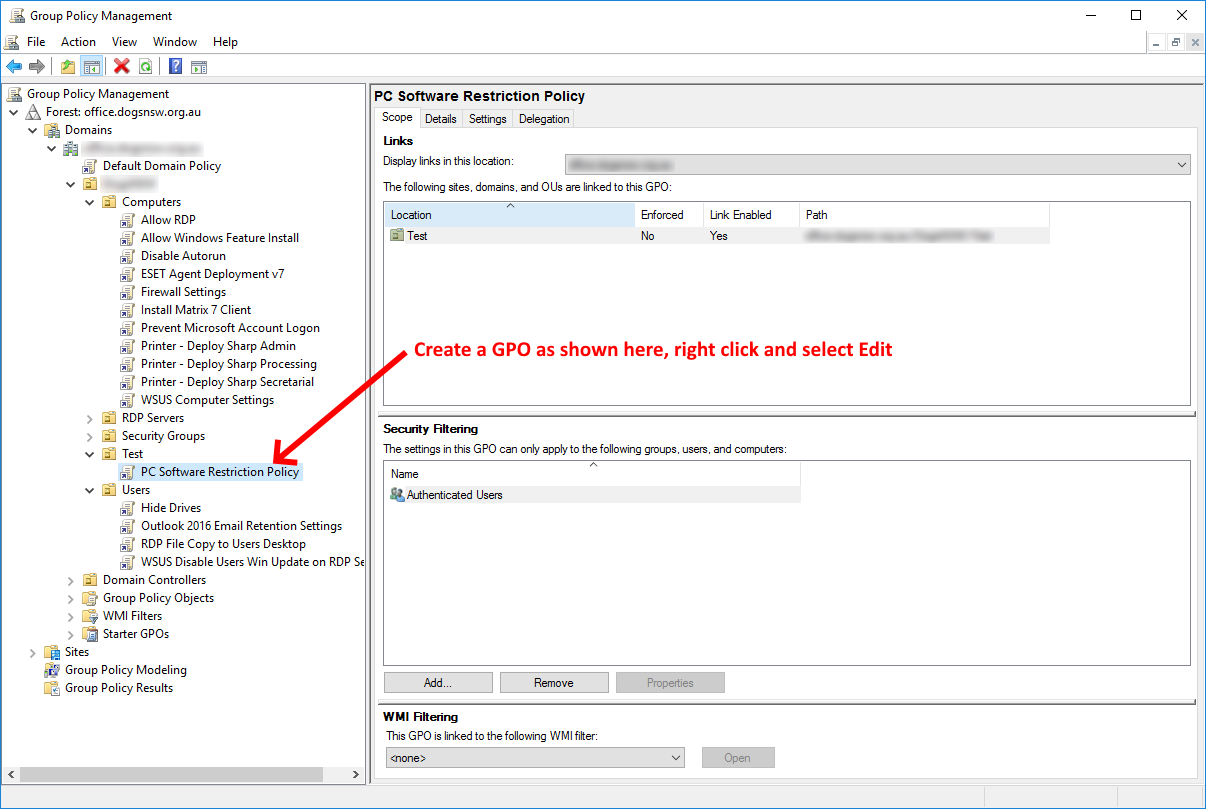
First, open up your Group Policy Management MMC and follow the screenshot below:
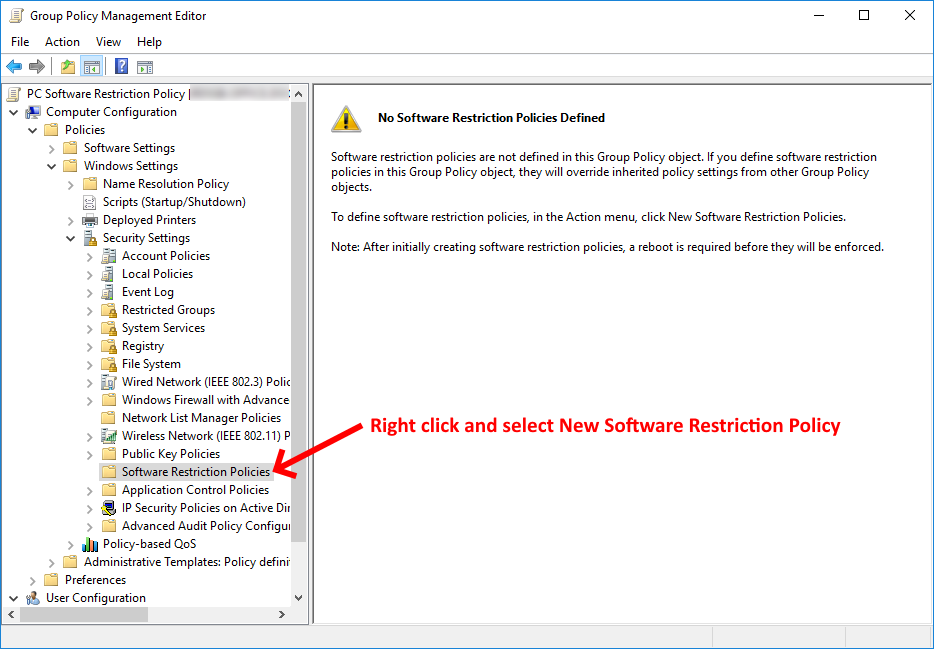
Once the Group Policy Management Editor has opened navigate to the following location:
Computer Configuration > Policies > Security Settings > Software Restriction Policies
Now follow the screenshots below:
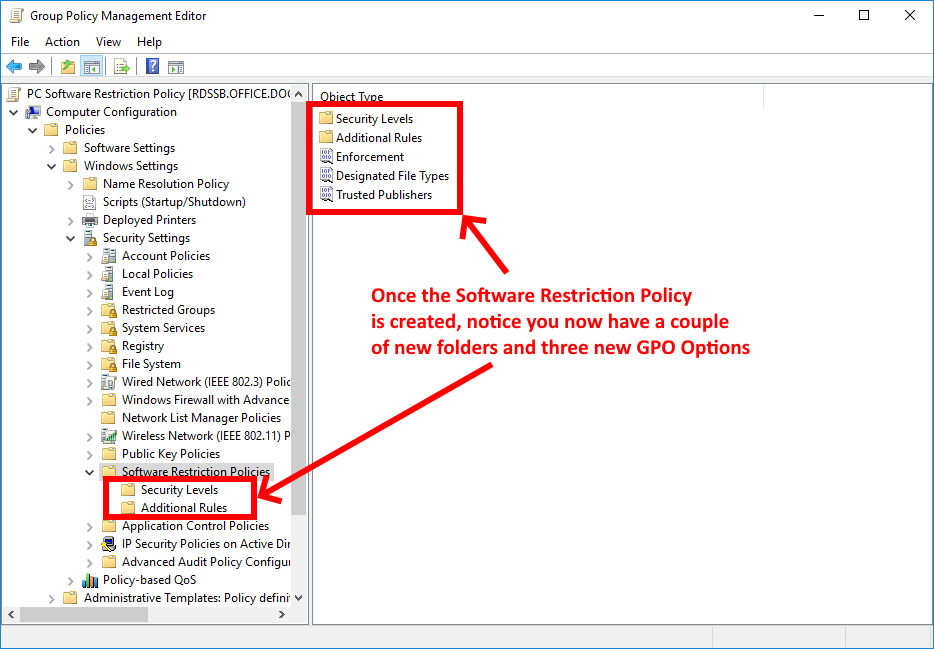
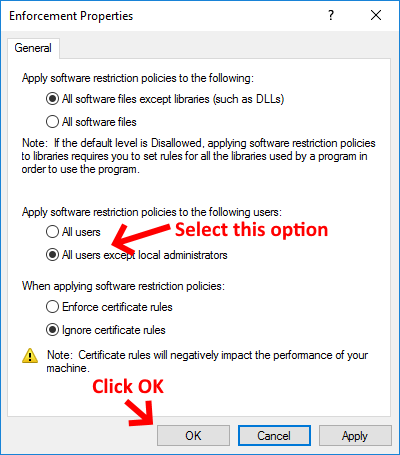
We're now going to going to edit the Enforcement GPO Option to allow administrators to run software, but prevent non-admin users from executing any software that is not authorised. To do this, right click on Enforcement and select Properties. Now select the options outlined in the screenshot below:
Now we're going to nominate the types of file extensions are going to be blocked by this policy. To do this, right click on Designated File Types and select Properties. From the resultant Designated File Types Properties window you can add and remove file types to suit your requirements. Here is a screenshot:
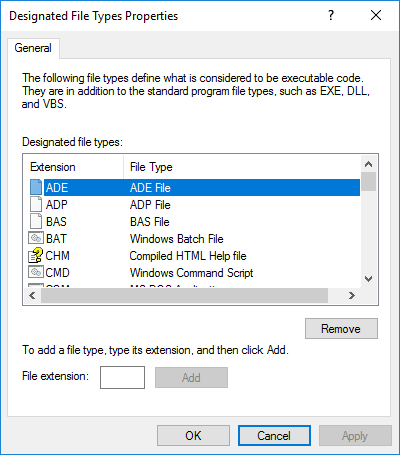
For this exercise I have left the Trusted Publishers option as disabled/undefined because I believe it adds too much complexity to the policy. Also, I need more time to evaluate the impact defining the policy will have on the SRP.
We're now going to go to the Security Levels folder within your SRP to apply the default security level you want for this policy. In my case I'm going to make Disallowed as the default. To do this, follow the screenshot below:
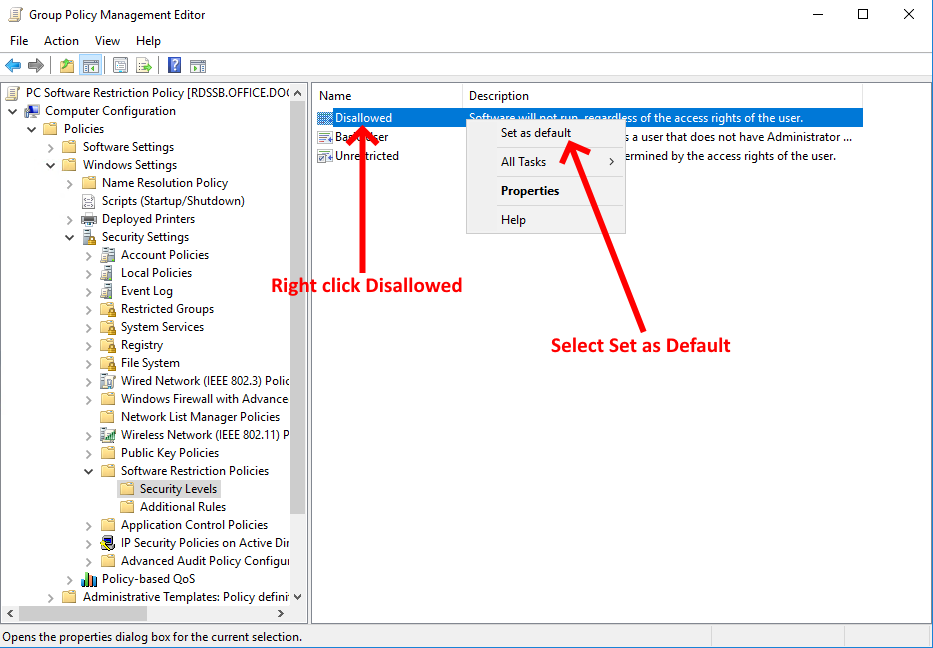
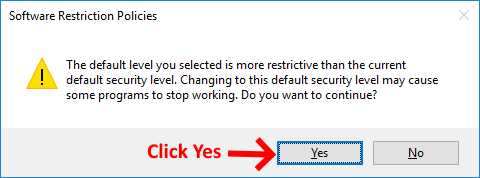
We've now setup an extremely restrictive SRP and your users will now struggle to run any applications which is not what we want. We need to allow them to run software so they can get their work done. So how do we do this?
By default everything in C:\Windows is allowed to run otherwise it would prevent vital services and programs running that allow your operating system to do what it does. We will need to allow both C:\Program Files and C:\Program Files (x86) to be whitelisted to allow installed applications to run. You can do this by following the procedure below:
The easiest method of allowing a location to be whitelisted is to setup a path rule. Follow the screenshots below:
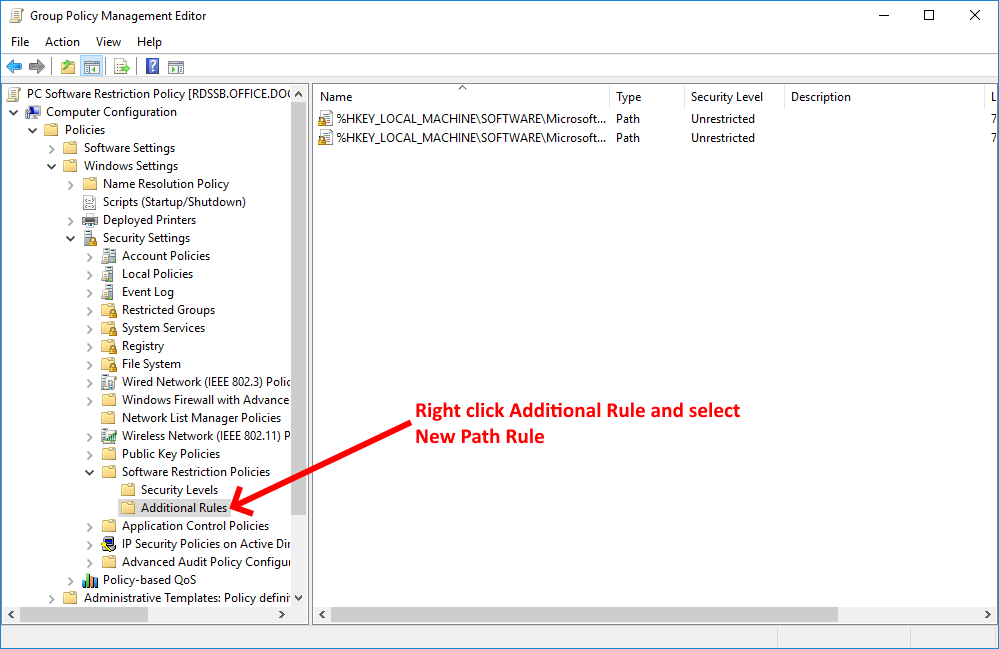
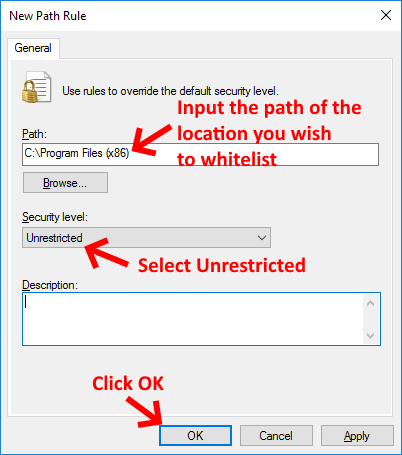
Create a path rule for both the C:\Program Files and C:\Program Files (x86) folders to ensure programs will run freely.
Some older programs that have been installed in the root of C:\ drive and other unusual locations will need to also be handled with a path rule to suit their specific requirements. This also applies to programs that are installed and run within the users profile like AppData folder. Once again, just make a path rule to exclude these locations.
Remember though, that the more lenient you are with the policy, the potential of a rogue application being executed on your network increases. So it advisable to err on the side of caution and be more explicit with your path rule. There is a whole detailed explanation of how path rules work here..
For instance, if you have an application that runs MYOB in the following location C:\MYOB, instead of creating a path rule as C:\MYOB which whitelists the entire folder and everything in it, be more explicit by including the file name to the executable, for example C:\MYOB\Myob.exe. That will increase the security and reduce the potential for a breach.
Also, you can use things like environmental variables in your path rule. For example, if you had putty.exe on each users desktop you could use the following:
%USERPROFILE%\Desktop\Putty.exe
The initial configuration of your SRP is complete. Now go to the test PC in your OU and reboot the machine to apply your new SRP. Log on as a standard user and test out if there are any applications that prevent your standard user to doing their daily tasks.
The final step is to debug issues when legitimate programs are blocked from running. How do you find what application and path have been blocked? The easiest method is by using Event Viewer. To open Event Viewer press the Windows Key + R on your keyboard and type in eventvwr.msc and press enter. Once the EV window opens expand Windows Logs and highlight Application. An example of a blocked file is in the screenshot below:
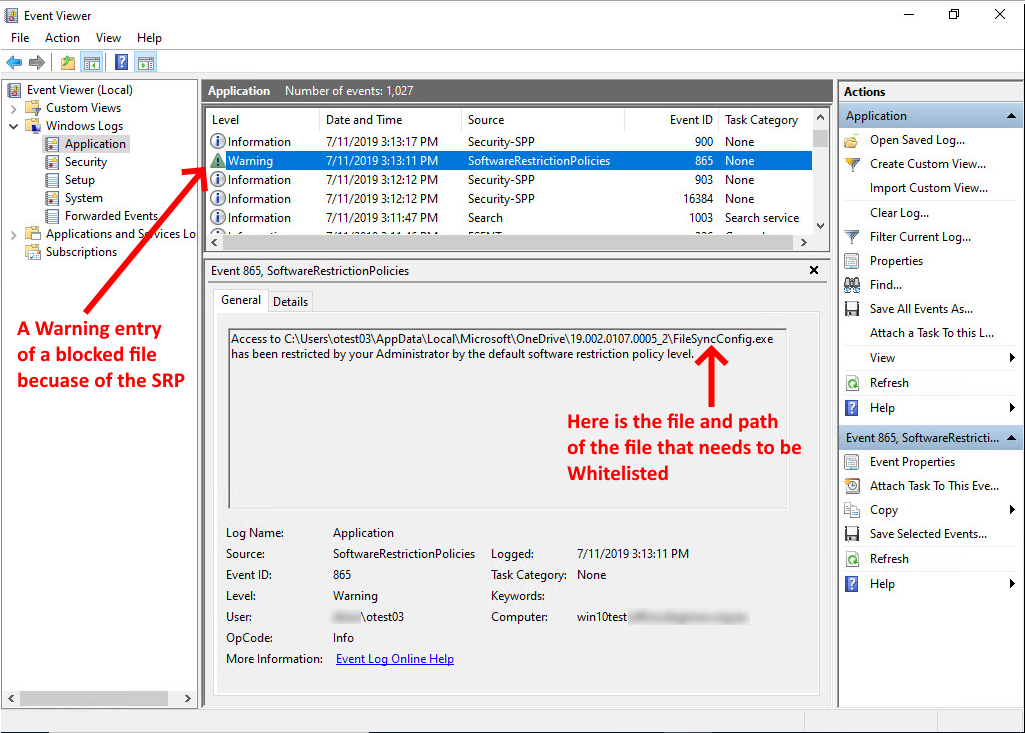
This does take quite a bit of configuration and setup, but once complete will give a more secure network and give you another tool to combat ransomware.
If you've found this useful, you may want to sign up to our newsletter where you'll receive notices on when we post new articles and helpful "how tos". Just fill out your details below and we'll do the rest...